Chillisoft Service Level Agreement (MDR, IDR)
1. Scheduled Maintenance
Scheduled maintenance is any maintenance that is performed by Chillisoft during a scheduled maintenance window (7:00PM NZT – 7:00AM NZT). Chillisoft will provide a 48-hour notice to its platform for any high-impact changes, excluding any unscheduled emergency maintenance that needs to be performed for stability or security of the platform.
2. Incident Investigation Procedure
2.1 Chillisoft will be responsible for alert analysis and investigation to determine if alerts or security events warrant alert classification or escalation. Chillisoft will follow established escalation paths and utilize contact information collected during the on-boarding process, as mutually agreed by the Customer and Chillisoft. It is the responsibility of the Customer to ensure that its contact information is correct, and any changes to the escalation paths or contact information should be communicated to Chillisoft immediately.
2.2 Chillisoft will investigate all initial security alerts identified and escalate alerts as appropriate in accordance with the established SLAs. If one or more events require the Customer’s escalation, Chillisoft will escalate the alert to the Customer for action. The Customer is responsible for responding to escalated alerts and comments in order to resolve escalated alerts. Chillisoft will perform alert triage, including determining the categorisation and prioritisation of the alert.
2.3 For alerts that are assigned to the Customer after analysis, the Customer is responsible for escalating alerts back to Chillisoft that require action or analysis by the Services. As events are pulled into the MDR workflow, it is Chillisoft’s responsibility to create and investigate alerts. As Chillisoft is responsible for alert escalation and response, only Chillisoft has the authority to investigate events or alerts to ensure due diligence of event investigation and accountability in reporting.
2.4 Additional responsibilities of Chillisoft include:
a) Producing internal reports on security activity and MDR workload metrics to include events ingested, alerts created, alerts escalated, and metrics around alert management. Additionally, reporting can include other pre-determined metrics around alert categorisation, priority, and SLAs.
b) Assisting in identifying potential impact of alerts on Customer systems and using data from the Services to assist the Customer in determining extent of impact.
c) Creating and reviewing playbooks to automate classification of false positives and events that the Customer has determined do not require escalation. Playbooks are security orchestration automation response features that automate classification and routing of security events.
d) Escalating alerts to identified Customer contacts for clarification and/or remediation.
2.5 Task ownership is outlined using a RACI model that adheres to the following format:

2.6 Chillisoft will include monitoring of alerts as well as detecting on proprietary Indicators of Compromise (IOCs). Task ownership is outlined below using a RACI Model.

3. Support Escalation Channels and Contacts
Chillisoft is committed to solving every case in a timely manner. If at any time the Customer is not satisfied with the level of support that it has received, it may contact Chillisoft’s security operation centre (SOC) management team by email at SOC@Chillisoft.net or by phone on 09 9737148.
4. File Analysis Submissions and Endpoint Isolation
4.1 Chillisoft conducts File Analysis Submissions and performs Isolation Services, each as defined below, unless the Customer opts out of such services.
4.2 File Analysis Submissions
Chillisoft conducts dynamic and static analysis of unknown binaries and unknown files to improve analysis, detection, and response to security threats that may impact the Customer’s environments (File Analysis Submissions). This process may require Chillisoft analysts to upload unknown binaries and/or files detected in Customer environments to dynamic sandbox and/or static analysis services such as VirusTotal. Chillisoft will not be responsible for this submission or for any act or omission by any online service. VirusTotal makes the metadata publicly available along with scan results from dozens of anti-virus products and makes the files available to VirusTotal partners. VirusTotal terms of service and privacy policies may be viewed here: https://support.virustotal.com/hc/en-us/articles/115002145529-Terms-of-Service .
4.3 Isolation Services
Unless the Customer opts-out, Chillisoft will isolate potentially compromised machines (Isolation Services). Chillisoft will manually isolate the machine using the endpoint solution and notify the Customer of the isolation via the alert write-up procedure for escalation. The machines will remain in isolation until the threat has been remediated or the Customer has specifically indicated that they accept the risk and request Chillisoft remove the isolation.
4.4 If the Customer opts to have Chillisoft remove the isolation from an affected machine:
a) Associated SLAs will be suspended until the discovered threat has been remedied; and
b) The Customer must waive all associated liability regarding the affected machine’s removal from isolation.
4.5 The Customer will identify production impacting servers and assets that are not to be isolated unless the Customer has given written authorization. Chillisoft will isolate machines that are not on the authorized list only to prevent the spread of malicious code and lateral movement by suspected attackers. Chillisoft will escalate all alerts that require isolation to the Customer for the Customer’s visibility and active feedback on the alert.
5. Incident Handling
5.1 Chillisoft will categorize and respond to Incidents according to the priority level. The priority of an incident is based on the Impact and Urgency of an incident. The table below explains the methodology of determining the priority levels.
Chillisoft follows TLP traffic light protocols regarding data severity as outlined below.
https://www.ncsc.govt.nz/protect-your-organisation/traffic-light-protocol/
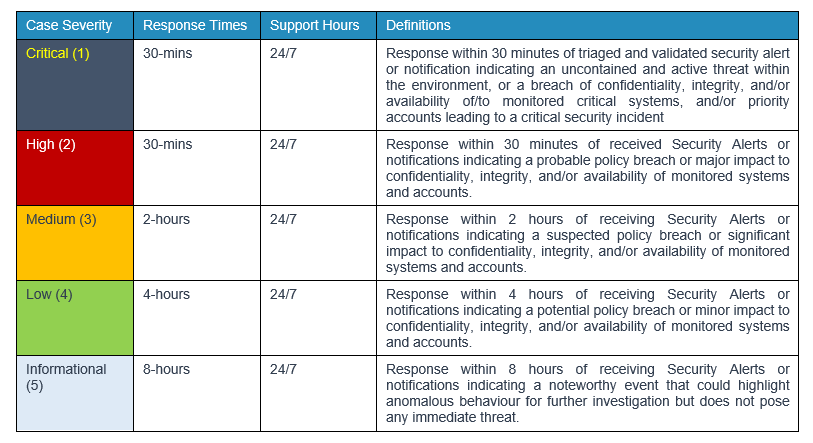
5.2 Chillisoft will adjust the case priority in accordance with updated priority of impact or incident resolution. In addition, the ticket may be left open after containment or restoration for a prescribed period while remediation efforts are being assessed.
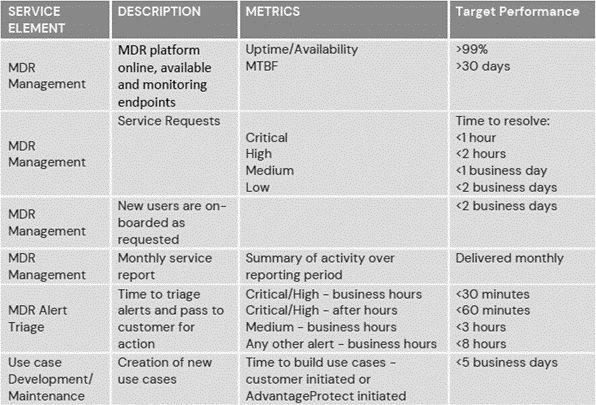
6. SLA Compliance
6.1 Tracking of SLA compliance starts when the deployment process has been completed, the devices and security controls have been set to live, and support and management of the devices and security controls have been successfully transitioned to the Services. The Customer will be notified in writing that the Services have transitioned from deployment phase to full production monitoring. SLAs will not apply, and remedies will not be available, for the beta, proof of concept, testing, implementation, and deployment phases of the Services.
6.2 The Customer (or Client) is responsible for responding to escalated alerts and comments in a reasonable timeframe, in order to resolve open alerts and create playbooks to remove future false positives. 3 Business Days from when an alert is escalated to the Customer is considered a reasonable timeframe. SLAs do not apply during periods of time when the Customer (or Client) is not responding to multiple requests to resolve open alerts and potential false positives.
6.3 Chillisoft reserves the right to amend the SLAs from time to time in its reasonable discretion by written notice to the Customer, provided such amendments:
a) will have no material adverse impact on the Services or SLAs currently being provided to the Customer by Chillisoft; and
b) are being affected with respect to all other similarly situated Chillisoft customers.
7. Exclusions from SLAs
The impact of any of the following items shall be excluded from the calculation of SLA achievement:
a traffic/events that do not reach the Chillisoft SOC due to:
i) The fault or delay of Customer (or Client); or
ii) A failure of the network environment, internet connectivity or traffic that does not generate a logged event;
b) Service interruptions, deficiencies, degradations, or delays due to:
i) Customer or Client supplied Internet or private access;
ii) Power, equipment, systems or services not supplied by Chillisoft;
iii) Equipment, configuration, routing event, or technology required for delivery of the
Services that are under the management or control of the Customer or Client;
iv) Customer or Client changes to the system specifications;
v) Removal of a service component by the Customer or Client without a mutually agreed to change order; or
vi) The acts or omissions of third parties engaged by the Customer or Client;
c) Performance of scheduled or emergency maintenance;
d) The Customer’s or Client’s noncompliance with any instruction provided by Chillisoft as to:
i) The deployment, adjustment, or maintenance of any software, policy, or license; or
ii) Recommended configurations on managed or unmanaged equipment that impacts the provision of the Services;
e) Failure to provide a suitable and secure environment for on-premises devices;
f) Network, software, or server changes or outages to the managed services environment without
reasonable prior notification that significantly impact event volumes. This applies to any assets that may affect the generation of and/or transmission capability of logs, and events or other activity which is monitored by Chillisoft for security alerts; or
g) Any time period during which the Customer or Client or a Customer or Client engaged third-party initiated testing of the Services is taking place.
8. Out of Scope Services
The Customer acknowledges that any cybersecurity event detected during the Service onboarding process that requires Chillisoft’s resources outside the scope of the Services under the Agreement will be subject to a separate cybersecurity event response retainer. Additional professional services may be required for such an engagement and, if required, will be captured in a Statement of Wor
