Log4Shell Explained: Remote Code Execution and Widespread Impact
Imperva blocked over 102 million Log4Shell exploit attempts! The Log4Shell zero day vulnerability is truly one of the most significant security threats of the past decade and its effects will be felt far into 2022 and beyond. Imperva has observed over 102M exploitation attempts across thousands of sites protected by Imperva Cloud Web Application Firewall (WAF). In the days following, the team at Imperva also responded to the additional Log4j-related vulnerabilities disclosed following the initial zero day publication, to ensure the best possible protection for our customers.
There is a wealth of resources readily available online that explain what each Log4j vulnerability is and how the exploits work. In this blog, we will demonstrate some of the interesting attack patterns, payloads, bypass techniques, and data points we have observed during our analysis of the recent Log4j related vulnerabilities. The data presented throughout this blog post is sourced from analyzing Imperva’s global network traffic and publicly-available external sources, including social media.
Imperva response to Log4shell
Although Imperva’s generic security rules provided protection against exploitation attempts, a few hours after the proof of concept (PoC) was published on December 9, Imperva security analysts deployed a dedicated mitigation and issued a manual mitigation guide for Imperva Web Application Firewall (WAF) customers.
Exploitation attempts
Imperva has blocked over 102M attack attempts since the disclosure on December 9. The following graphs illustrate how the attacks have developed.
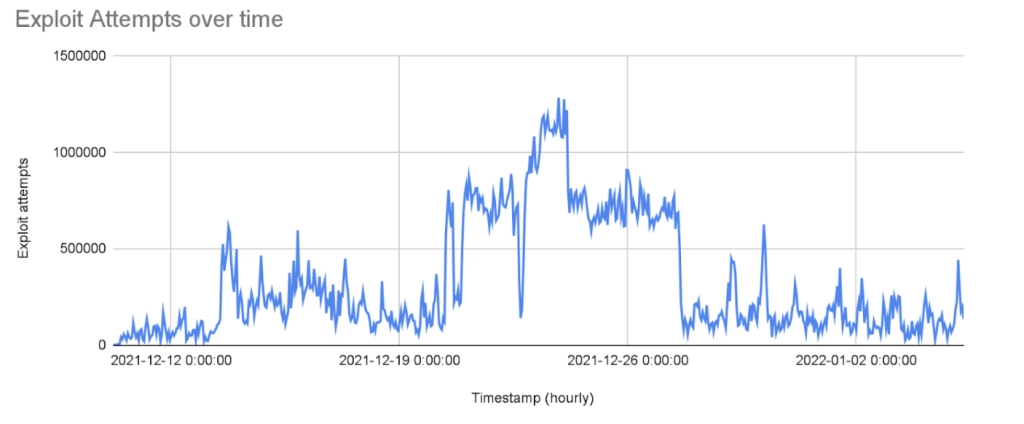
Exploit attempts over time
The following graph shows the volume of exploit attempts against sites onboarded to Imperva Cloud WAF since the disclosure of the vulnerability. Imperva observed almost 1.3M exploit attempts per hour within the first 10 days of the exploit becoming public. Since the peak on December 23, we have observed a general declining trend in the number of exploit attempts.
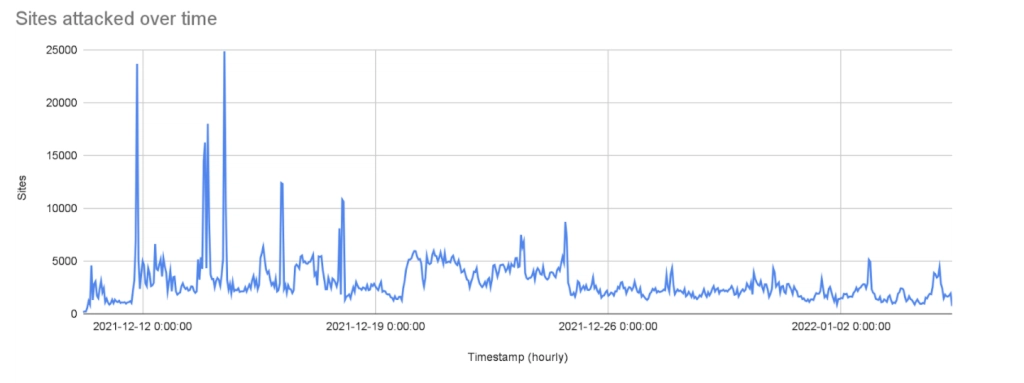
Sites attacked over time
In addition to the astounding rate of exploit attempts, the number of sites targeted was also remarkable, reaching a peak of 25K sites attacked per hour. This can be explained by the preponderance of Java-based web applications and how ubiquitous the Log4j package is across these applications. Attackers appear to be using “spray and pray” and fuzzing techniques to identify vulnerable applications.
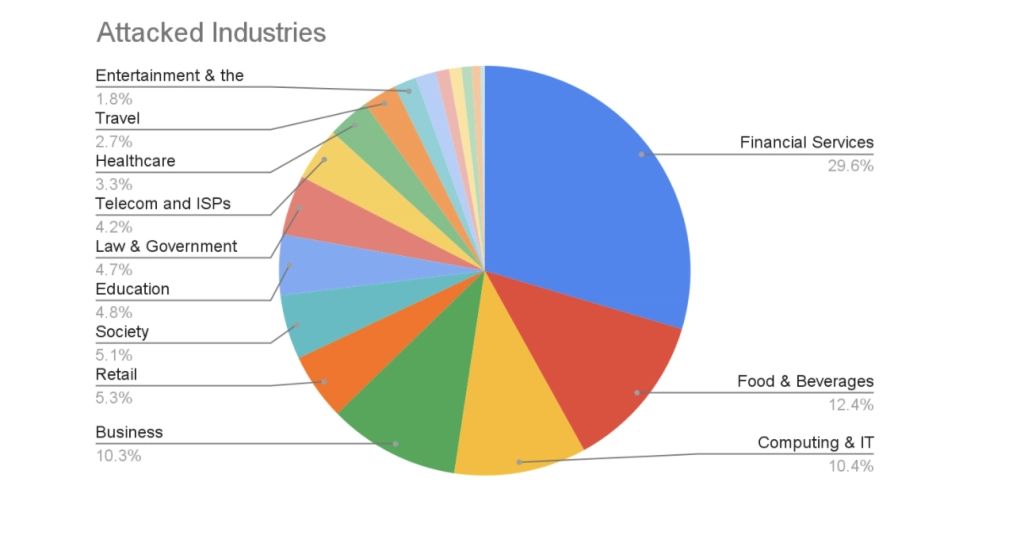
Attacked industries
The following chart shows the breakdown of exploitation sessions by industry. At the time of writing the most commonly targeted industries are Financial Services (29.6%), Food and Beverages (12.4%) and Computing and IT (10.4%). As we mentioned previously, attackers largely used a “spray and pray” approach to the exploitation of this vulnerability, and we did not detect a strong correlation between the top sites attacked in each category and their technology stack, however, the correlation becomes more observable when considering only malicious remote code execution (RCE) payloads which appear to be more targeted.