Enterprise-Level Identity Detection & Response, for any business customer.


Enterprise-Level Identity Detection & Response, for any business customer.
As cyber attack strategies are growing in complexity and in turn cybersecurity is arguably better and more advanced than ever, those that seek to breach defences are increasingly turning to social engineering and identity-based attacks in order to gain access to login credentials. With any stolen credentials, bad actors are only so limited as to the access the given user has. A successful breach even on a low-rank user often gives access to data which helps refine attacks targeted higher users or gain partial access where they can lurk and wait for opportunities to advance their attack.
Chillisoft’s Managed Identity Detection enables identification and 24/7 response to threats targeting your organization’s identity infrastructure, such as user accounts, credentials, and identity-related systems. Our service consists of live monitoring, analysis, and automated response using the alarms and alerts generated by MSFT Entra. Our multi tenanted white labelled service will help our partners and customers rest easy knowing you’re protected from risks associated with identity-based attacks. Our white labelled IDR service along with our MDR service is designed to work together to better detect, protect and respond when under attack.
Save your company from credential breaches, rest easy as you rely on Chillisoft for your Managed Identity Protection
Session Takeover
Prevent intruders from compromising your systems.
Impossible Travel
Monitor, deny login, respond to impossible travel & action.
Eg. Login from Auckland quickly followed by login from Vegas.
Escalated Privileges
Prevent unauthorized access and ensure control remains with the right users.
Credential Harvesting
Keep attackers out by securing and monitoring your identity assets.
Email rule anomalies
See suspicious activity, keep emails secure and private while safeguarding your inboxes.
Effective IDR combines identity attack signals with endpoint monitoring through ESET XDR, providing a comprehensive approach to threat detection and response. Microsoft Entra logs are continuously analysed across environments to identify anomalies such as impossible travel, where a user’s login attempts from disparate locations, like Auckland and Singapore, flag potential identity misuse. Analysts swiftly confirm compromise, escalate incidents, and take corrective actions, including blocking accounts and resetting passwords. Correlating identity data with endpoint activity uncovers malicious behaviours, such as unauthorized installations or system scans tied to compromised accounts. Following thorough investigation and mitigation, the analyst provides a detailed report to the customer with findings, remediation steps, and recommendations for securing the affected systems.
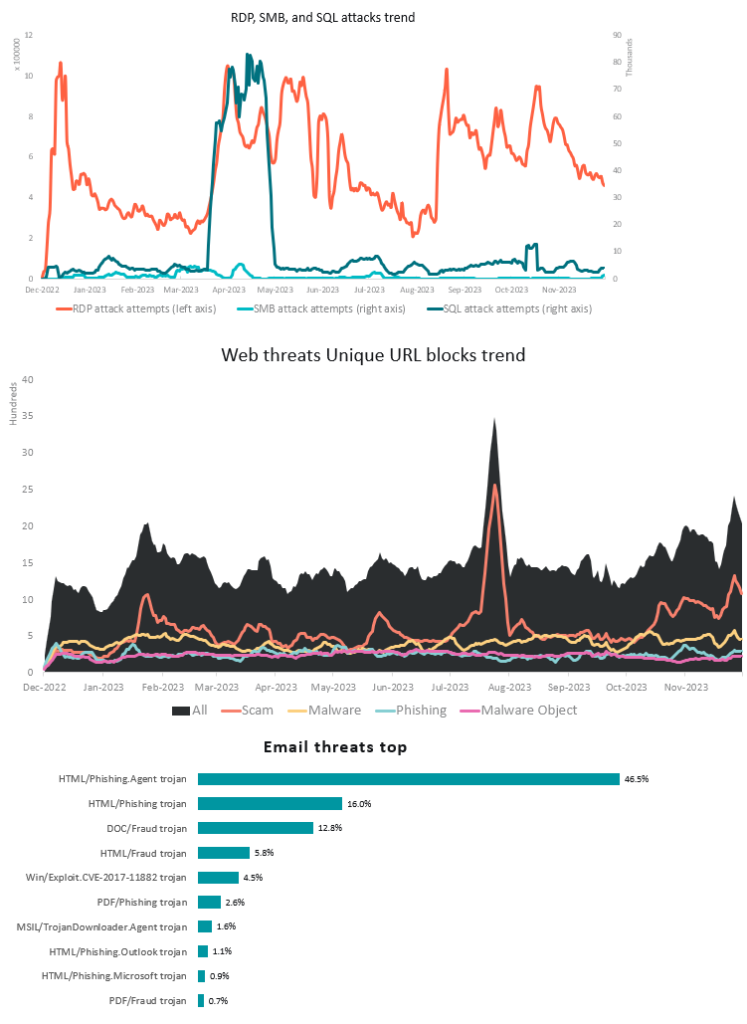
By far, phishing is the main breach format Kiwi’s are attacked by, comprising of 46.5% of attacks in New Zealand in 2023 and similarly over 2024. The root aim of phishing is social engineering. This is the manipulation of people into extraction of confidential or personal information, performing actions, or granting access to systems. Instead of directly hacking into systems, attackers exploit human psychology and behaviour to achieve their goals. While phishing is the main attack type, social engineering is not limited to any one attack method and can also take place in forms like pretexting, baiting or even in-person tail gaiting.
Relying on simple tactics seems crude at first, however the complexity of attacks are becoming far more articulated and refined! Bad actors are now commonly using AI to scan public data and help them increase the relevance of social engineering messages. As attack messages, fake landing pages and source mimicking are all enhanced, purposeful targeted attacks are appearing more authentic than ever!
A successful breach, even on a low-rank user, can lead to attackers gaining access to data which helps refine further attacks, targeted higher users. Even partial access can be enough for attackers to gain access to sensitive and private information. At the very least, low level access affords hackers a perch from where they may lurk and wait for opportunities to advance their attack.
Peace of mind with Chillisoft’s IDR
24/7 Kiwi Care
Rely on comprehensive visibility with expert monitoring of your identity attack surface.
Proactive Action
Proactively safeguard your business-critical assets with advanced detection and response.
Block dodgy logins
Stop suspicious logins in their tracks before they have the chance to disrupt your operations.
Reveal hidden workflows
Proactively identify and eliminate hidden threats to shield your business from stealthy cyberattacks.
Focus on threats
Working with Chillisoft, you’ll have clarity as we eliminate false positives and verify real threats.
30 day free trial
*(Must be licensed with Entra).
Chillisoft MDR customers will be offered Identity Detection Response for free!
The free offer on Identity Detection Response is available for new MDR customers from the 13th of January 2025.
Existing customers are also eligible, however, they must sign a new MDR contract which includes IDR.
All customers must buy their own Microsoft Entra Licenses.
Airtight protection of your IT environment, with complete cyber risk management and world-class ESET expertise on call.
Cyber risk management and visibility into your IT environment managed from a single pane of glass console that can be installed on premises or cloud-based, depending on your requirements.
Get in touch with us to discuss MDR.
