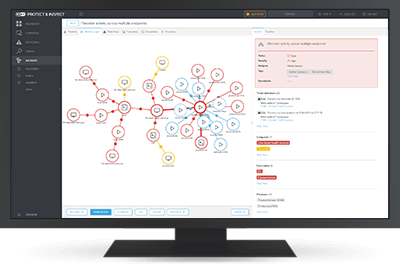
Today, organizations need increased visibility into their endpoints, devices, and network to ensure that emerging threats, risky employee behavior, and unwanted applications do not risk their profits or reputation. ESET Inspect is the cloud-delivered, XDR-enabling module of the ESET PROTECT platform. It provides unique behavior – and reputation-based detection that is fully transparent to security teams, giving them real-time feedback based on threat intelligence provided by the global ESET LiveGrid® reputation system.

XDR SOLUTION
ESET EXTENDED DETECTION & RESPONSE
Extended detection and response (XDR) from ESET empowers you to quickly and effectively identify anomalous behavior and breaches, and provides advanced threat hunting, risk assessment, incident response, investigation and remediation capabilities.
Why do customers appreciate our XDR solution?
Expertise
Detection and response from a trusted, research-based, security-first vendor with 30 years’ experience at the cutting edge of digital security
Quality
Tightly integrated with ESET’s multilayered prevention products, based on technology that has won numerous awards and is recognised industry-wide
Flexibility
It works out-of-the-box with automated incident creation and remediation. For experienced threat hunters and incident responders, there are granular controls for optimal tailoring for specific requirements
Transparency
Detailed network visibility across multiple layers – including email, network attack protection, anti phishing, servers – with transparent detection rules
Secure your digital life with ESET:
Next-Gen Cybersecurity You Can Trust
The XDR-enabling module of the ESET PROTECT platform, delivering breach prevention, enhanced visibility and remediation.
Also available as part of our MDR Service.
What makes ESET's solution a perfect fit for your needs?
Extended detection & response
ESET Inspect
Provides risk managers and incident responders with outstanding threat and system visibility, allowing them to perform fast and in-depth root cause analysis and immediately respond to incidents. Paired with the time-tested prevention power of ESET PROTECT Platform, ESET Inspect is a cloud-delivered, XDR-enabling solution to:
- Detect advanced persistent threats
- Stop fileless attacks
- Block zero-day threats
- Protect against ransomware
- Prevent company policy violations
Explore ESET Inspect features
Public API
ESET Inspect features a Public REST API that enables the accessing and exporting of detections and their remediation to allow effective integration with tools such as SIEM, SOAR, ticketing tools and many others.
Multiplatform coverage
ESET Inspect supports Windows, macOS, and Linux, which makes it a perfect choice for multiplatform environments.
MITRE ATT&CK™
ESET Inspect references its detections to the MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK™) framework, which in one click provides you with full data about even highly complex threats.
Automated incident visualization
Get perfect visibility with automatically created and clearly visualized incidents. ESET Inspect correlates vast amounts of data to find root cause events and compile them into comprehensive incidents so that you can resolve them immediately.
Save and smooth remote access
Incident response and security services are only as smooth as the ease with which they are accessed – both in terms of the incident responder’s connection to the XDR console, and the connection with the endpoints. The connection works at close to real-time speed with maximum security measures applied, all without the need for third-party tools.
One-click isolation
Define network access policies to quickly stop lateral movement by malware. Isolate a compromised device from the network with just one click in the ESET Inspect interface. Also, easily remove devices from the containment state.
One-click isolation
Define network access policies to quickly stop lateral movement by malware. Isolate a compromised device from the network with just one click in the ESET Inspect interface. Also, easily remove devices from the containment state.
Anomaly and behavior detection
Check actions carried out by an executable and utilize ESET’s LiveGrid® Reputation system to quickly assess if executed processes are safe or suspicious. Monitoring anomalous user-related incidents is possible due to specific rules written to be triggered by behavior, not simple malware, or signature detections. Grouping of computers by user or department allows security teams to identify if the user is entitled to perform a specific action or not.
Tagging
Assign and unassign tags for fast filtering of objects such as computers, alarms, exclusions, tasks, executables, processes, and scripts. Tags are shared among users, and once created, can be assigned within seconds.
Multiple Indicators of compromise
View and block modules based on over 30 different indicators, including hash, registry modifications, file modifications and network connections.
Live response options
Our XDR comes packed with easily accessible oneclick response actions such as rebooting and shutting down an endpoint, isolating endpoints from the rest of the network, running an on-demand scan, killing any running process, and blocking any application based on its hash value. Additionally, thanks to ESET Inspect’s live response option, called Terminal, security professionals can benefit from the full suite of investigation and remediation options in PowerShell.
Flexibility of deployment
We let you decide how to deploy your security solution: It can run via your own servers on-prem, or via a cloudbased installation, allowing you to tune your setup according to your TCO targets and hardware capacity.
Interactive behavioral reports
Encountered a suspicious file? Submit it for in-depth analysis to ESET LiveGuard Advanced, equipped with powerful cloud sandbox. Within moments, view an interactive report on the file’s behaviors, system changes, API calls, etc. and block it all.
Automated incident visualization
Get perfect visibility with automatically created and clearly visualized incidents. ESET Inspect correlates vast amounts of data to find root cause events and compile them into comprehensive incidents so that you can resolve them immediately.
Threat Hunting
Use the powerful query-based IOC search and apply filters to raw data for sorting based on file popularity, reputation, digital signature, behavior, or other contextual information. Setting up multiple filters allows automated, easy threat hunting and incident response, including the ability to detect and stop APTs and targeted attacks.
Open architecture and integrations
ESET Inspect provides unique behavior- and reputationbased detection that is fully transparent to security teams. All rules are easily editable via XML to allow finetuning or easily created to match the needs of specific enterprise environments, including SIEM integrations.
Incident Management System
Group objects such as detections, computers, executables or processes into logical units to view potential malicious events on a timeline, with related user actions. ESET Inspect automatically suggests to the incident responder all related events and objects that can greatly help in an incident’s triage, investigation, and resolution stages.
Company Policy Violation Detection
Block malicious modules from being executed on any computer in your organization’s network. ESET Inspect’s open architecture offers the flexibility to detect violations of policies that apply to the use of specific software like torrent applications, cloud storage, Tor browsing or other unwanted software.
Sophisticated scoring
Prioritize the severity of alarms with a scoring functionality that attributes a severity value to incidents and allows admins to quickly identify computers with a higher probability for potential incidents.
Local data collection
View comprehensive data about a newly executed module, including time of execution, the user who executed it, dwell time and the devices attacked. All data is stored locally to prevent sensitive data leakage.
Root Cause Analysis
Easily view the root cause analysis, and full process tree, of any potentially malicious chain of events, drill down to the desired level of detail and make informed decisions based on the rich provided context and explanations for both benign and malicious causes, written by our malware experts.
Root Cause Analysis
Easily view the root cause analysis, and full process tree, of any potentially malicious chain of events, drill down to the desired level of detail and make informed decisions based on the rich provided context and explanations for both benign and malicious causes, written by our malware experts.
Reputation system
Extensive filtering enables security engineers to identify every known good application, using ESET’s robust reputation system, so your security teams can focus on threats, not false positives.
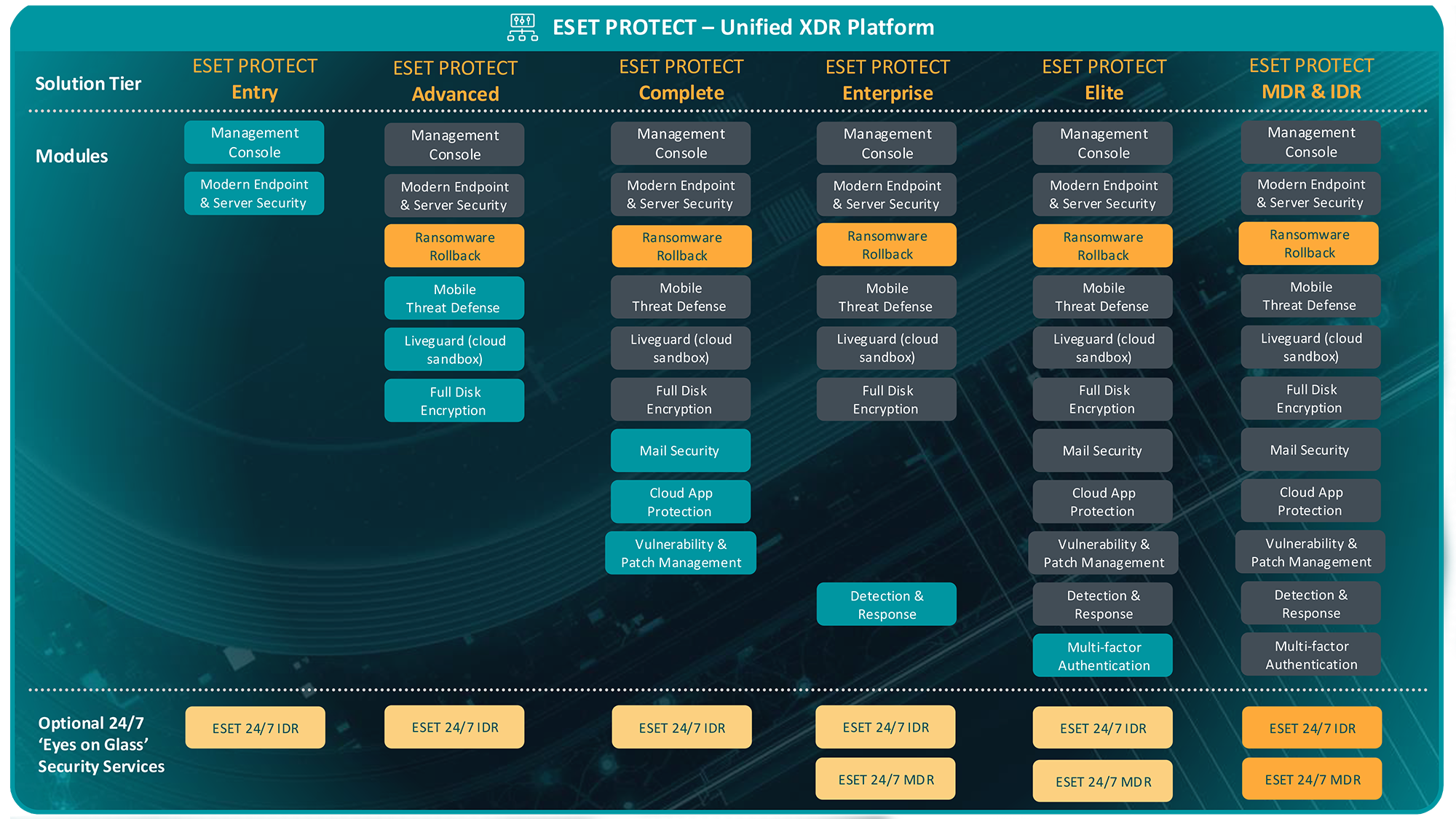
ESET PROTECT - UNIFIED XDR PLATFORM
GET THE RIGHT SOLUTION FOR YOUR BUSINESS NEEDS
ESET Protect Enterprise scored highly in the EPR Strategic Leader Quadrant in the recently published Endpoint Prevention and Response (EPR) Comparative Report 2024 by independent testing house AV-Comparatives. ESET stopped and reported most attack scenarios early, neutralizing remaining threats in the second phase. As a result, ESET achieved top rankings in prevention, detection, response, and reporting.
“ESET has proven its strength in endpoint security and EDR, earning recognition as a Strategic Leader for the fourth time since the certification’s introduction. Notably, ESET’s exceptional performance is also recognized in the leading Business security benchmarks, setting it apart in the industry“
Stated by Andreas Clementi, CEO & Founder of AV-Comparatives.

Consistently validated by customers worldwide
4.6
GARTNER PEER INSIGHTS
8.9
TRUSTRADIUS
4.7
CAPTERRA
4.6
G2
4.1
TRUSTPILOT

TRUSTED BY SOME OF THE WORLD'S BIGGEST PLAYERS


Talk to us about ESET
Chillisoft will help you understand how ESET can help with your security needs.