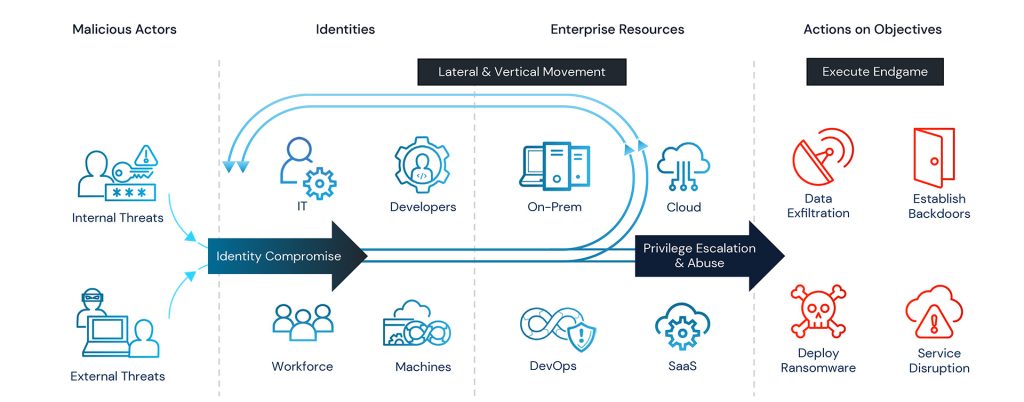
There is more to Privileged Access Management (PAM) than what meets the eye. In this dynamic and thought-provoking discussion, we will explore the concept of “Reimagining Privileged Access Management” and touch on various dimensions of PAM that extend beyond traditional paradigms of vaulting and into Identity Security. Join us as we reimagine PAM and uncover its ever-evolving role in the modern security landscape.
Featuring Piyush Ranjan, CyberArk ANZ Senior Solutions Engineer who will guide you into the world of Modern PAM.
In this webinar we cover:
- Gaining a comprehensive understanding of the evolving landscape of Modern Privileged Access Management beyond traditional vaulting paradigms.
- Explore the intersection between PAM and Identity Security, uncovering synergies and best practices for enhanced your organization’s cybersecurity posture.
- Acquire actionable insights for addressing emerging security challenges and its significance in safeguarding organizational assets.”