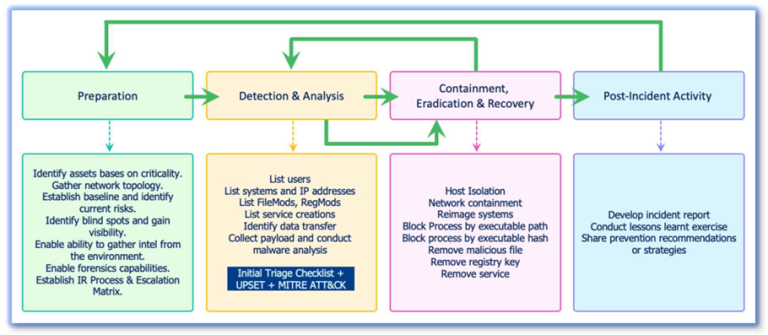
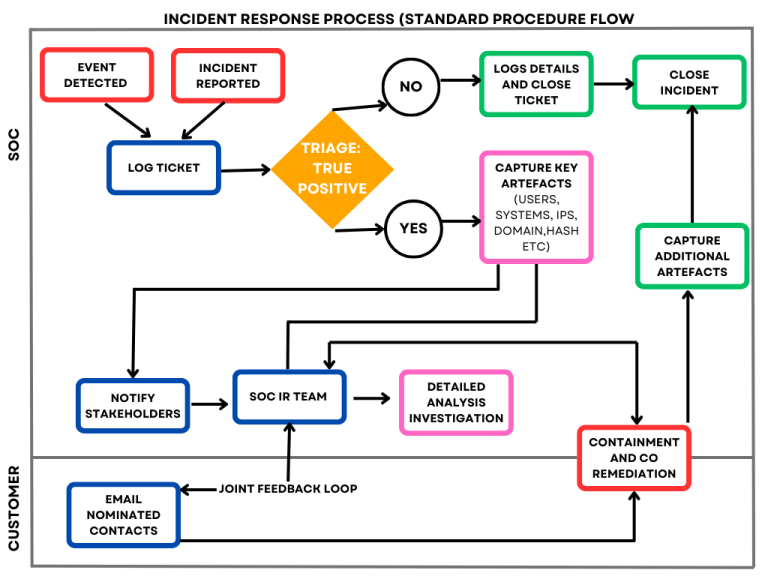
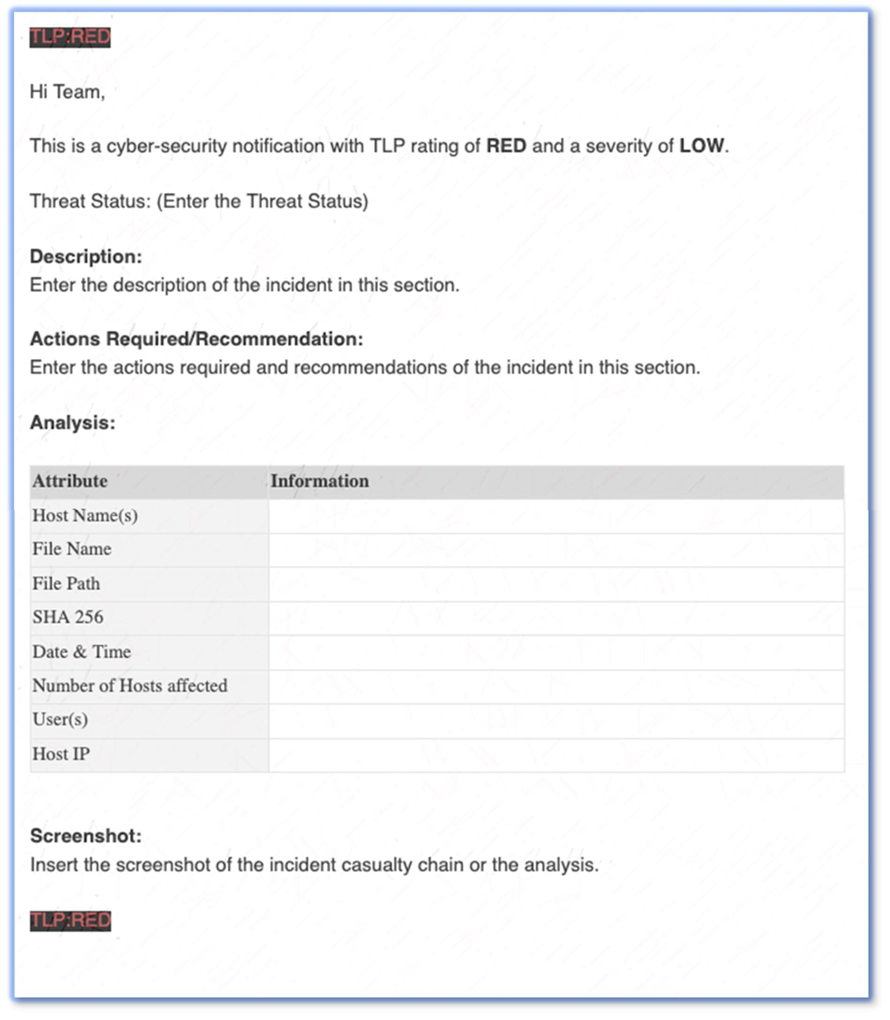
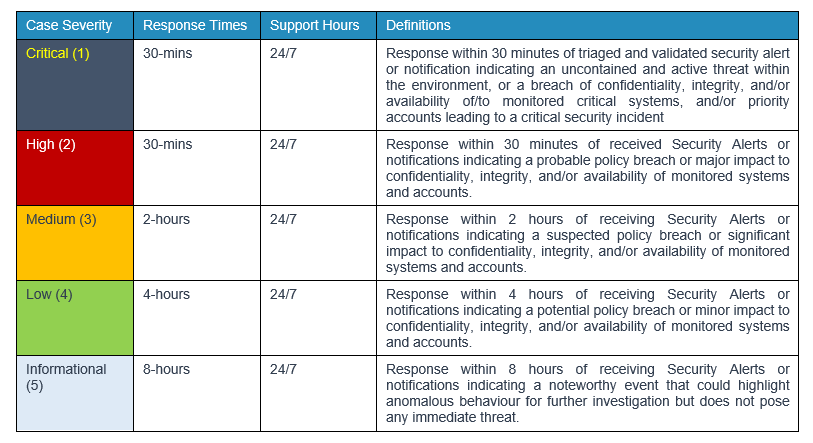
Roles and responsibilities for the various parties involved in all the steps of the incident response process are outlined below.
5.1 Incident Detection and Recording
Incidents may be discovered and reported by SOC Analysts or Threat Hunters. The individual discovering an incident should immediately contact the customer.
All CHILLISOFT employees being alerted to a suspected or confirmed incident, (whether part of the SOC or not) should endeavour to capture the following incident details as clearly as possible:
- The name of the individual who discovered the incident, and their contact details.
- Date and time of the reported incident.
- The nature of the incident, how and when it was detected.
- The customer stakeholders involved, and locations. Name of system being targeted, along with user, operating system, IP address, and location.
- Any information about the origin of the attack, including IP addresses, if applicable.
- Preliminary evaluation of the severity or impact of the incident.
The CHILLISOFT’s shift incident commander, working with customer stakeholders and their IT teams will be principally responsible for the Incident Ownership, Monitoring and Tracking on CHILLISOFT end.
CHILLISOFT’s shift incident commander will consider the following:
- Is the incident still in progress?
- What data or property is threatened and how critical is it?
- Is the incident still in progress?
- What is the impact on the business should the attack succeed?
- What system or systems are targeted, where are they located physically, and on the customer’s network?
- Is the incident inside the trusted network?
- Is an urgent response necessary?
- Can the incident be contained?
- What type of incident is this? Ex: virus, worm, intrusion, abuse, damage.
- What is the degree of confidence that the nature and impact of the Incident is fully understood?
A security incident report will be created. The incident will be categorised into the highest applicable severity as listed below.