Zero trust is a concept of applying the least amount of trust possible to allow an entity the ability to access the resource it requires to complete the assigned or needed task. This architecture works on the principle there is no implicit trust or baseline access to a resource, removing the concept of trusted by location as seen with the classic perimeter defense system. Unfortunately, many organizations are still relying on systems built with implicit trust in mind. Once something is inside the network perimeter, it can move laterally, unchecked. The solution is Zero Trust. More and more organizations are moving forward with a zero trust architecture, in order to improve cyber resiliency and better protect their networks from cyberattacks, expand remote work, modernize technology infrastructure, accelerate cloud adoption, and provide secure access to external partners.
Many organisations have made progress in implementing zero trust architectures and deploying technologies like security service edge (SSE) so they can leverage cloud environments and implement work-from-anywhere in a secure manner. Gartner predicts “by 2025, 80% of enterprises will have adopted a strategy to unify web, cloud services, and private application access using a SASE/SSE architecture by 2025, up from 20% in 2021.”
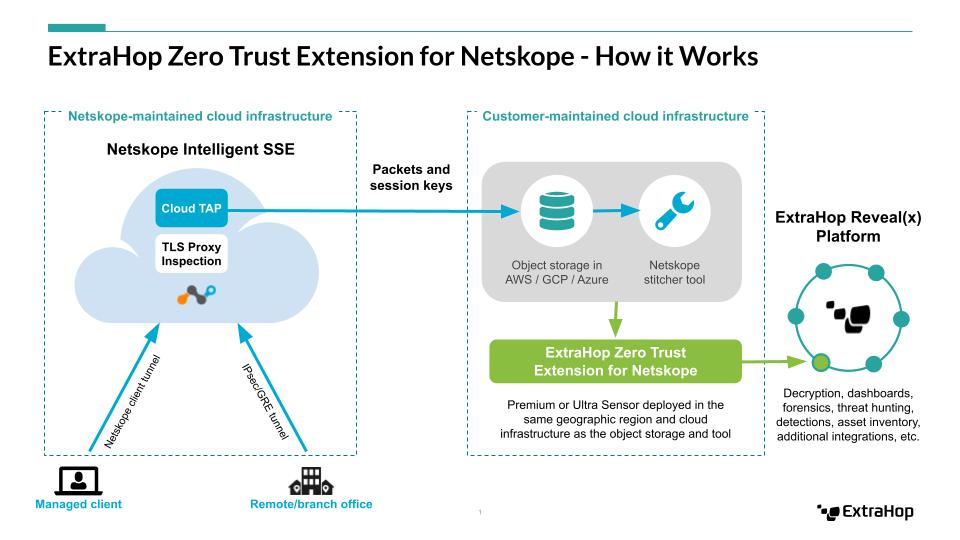
However the secure tunnels created by SSE means that network visibility tools like NDR and NAV can’t inspect this traffic, which leaves security and IT teams with a blind spot. The new integration between Netskope and ExtraHop is designed to address this problem. The Netskope Cloud TAP in combination with the ExtraHop Zero Trust Extension for Netskope, provides enterprises with unprecedented visibility into behavior and communication among devices and services in remote and distributed networks, across on-premises, hybrid, and cloud deployments, at any scale. Join us for this in-person event as we deep dive into the Zero Trust Integration between ExtraHop and Netskope.